|
Cryptome DVDs are offered by Cryptome. Donate $25 for two DVDs of the Cryptome 12-years collection of 46,000 files from June 1996 to June 2008 (~6.7 GB). Click Paypal or mail check/MO made out to John Young, 251 West 89th Street, New York, NY 10024. The collection includes all files of cryptome.org, jya.com, cartome.org, eyeball-series.org and iraq-kill-maim.org, and 23,000 (updated) pages of counter-intelligence dossiers declassified by the US Army Information and Security Command, dating from 1945 to 1985.The DVDs will be sent anywhere worldwide without extra cost. | |||
Table of Contents of main report.
FM 100-6 INFORMATION OPERATIONS
Effective battle staff planning requires a framework that focuses on the commander's concept of operation. Planners integrate all available information and resources that facilitate mission accomplishment at the strategic, operational, and tactical levels. This appendix discusses the INFOSYS support planning principles, signal support requirements, and C2W planning process the commander uses to plan and conduct military operations. The principles serve as a starting point from which to create solutions to mission requirements that focus on resolving all INFOSYS and C2W issues and problems before the start of operations.
The INFOSYS planning principles are derived from Joint Publications 6-0 and 6-02. These principles focus the planners' attention on what is important to the commander. The principles outlined here help accomplish this effort.
Modular INFOSYS packages consist of sets of equipment, people, and software tailorable for a wide range of missions. Planners must understand the mission, the commander's intent and operational plan, availability of assets, and the information structure required to meet the needs of each mission. These packages must satisfy the commander's informational requirements during the execution phases of the mission. Modular INFOSYS packages must be flexible, easily scaled, and tailored with respect to capacity and functional capability.
Interoperability is the capability of INFOSYS working together as a system of systems. Interoperability implies compatibility of combined, joint, and service common information or data elements procedures. Interoperability is the foundation on which INFOSYS capabilities depend. An interoperable INFOSYS is visible at all functional levels--a secure, seamless, cohesive, infrastructure that satisfies C2 and information requirements from the NCA to the lowest information request. INFOSYS should comply with the Army's technical architecture. Adherence to these standards and protocols helps ensure interoperability and a seamless exchange of information among the battlefield functional areas and joint services. Older INFOSYS that do not comply with the common operating environment and technical architecture require special planning and may not be interoperable.
LOs provide a means for the commander and planners to increase interoperability during different phases of an operation and between commanders and staffs that have not previously worked together. LOs are especially important for interpreting intent and relevance to the parties they serve and in overcoming the natural friction that develops between disparate organizations. LOs ease technical coordination and enable planners to manage information more efficiently and effectively. LOs are especially important when working with government agencies and allies.
Planners must be flexible when supporting INFOSYS requirements in changing situations. They must anticipate the possibility of changes in the mission or tactical situation and build a plan to accommodate them.
Scalable system packages ease the application of economy. Space, weight, or time constraints limit the quantity or capability of systems that can be deployed. Information requirements must be satisfied by consolidating similar functional facilities integrating commercial systems
INFOSYS must be reliable, robust, resilient, and at least as survivable as the supported force. Distributed systems and alternate means of communications provide a measure of resilience. Systems must be organized and deployed to ensure that performance under stress degrades gradually and not catastrophically. Command procedures must be capable of adaptation to cope with degradation or failure.
From an INFOSYS network perspective, planners provide diverse paths over multiple means to ensure timely, reliable information flow. From an equipment perspective, planners ensure that sufficient backup systems and repair parts are available to maintain the system's or network's capabilities.
The commander's information requirements must not be compromised by the use of nonstandard equipment. Planners must ensure that the equipment, its configuration, and the installed operating systems included in a modular package are standardized throughout the joint force. Standardization also includes INFOSYS training, symbology, switch network diagrams, packet network diagrams, and terminology.
The availability of commercial INFOSYS often offers the commander a guide, as well as an alternative means, to satisfy his informational C2 needs. Further, it may reduce the number and size of deployed modular packages; however, security must be considered. Operational use of a commercial system allows planners to compensate for system shortages and to meet the surge of information requirements in the early stages of deployment. The G6 has staff responsibility for the standardization of commercial equipment and software used throughout the AO. However, planners have to ensure the deployed modular INFOSYS packages implement open, nonproprietary, commonly accepted standards and protocols to interface with commercial systems.
The level of security depends on the nature of the information to be protected and the threat of interception or exploitation. Electronic on-line encryption devices usually provide communications security. Controlling physical access to terminals, software, and disks helps to ensure security of INFOSYS. Security must be balanced by the need to disseminate critical information quickly.
Throughout all force-projection stages, signal support must provide the means to transport information from CONUS sustaining-base installations, through strategic gateways, to the forward-most deployed units. The signal support requirements to fulfill this mission are critical to the successful execution of IO and are METT-T-dependent. Building on the essential tasks for INFOSYS described in Chapter 5, the INFOSYS planning process consists of five phases. These phases take the planner from construction through reconstitution of the INFOSYS.
The security aspects of occupying a dispersal area are pretty standard. What is new is the notion of establishing a sanctuary operations center--a place from which to anchor the unit's INFOSYS. It may actually be in CONUS or aboard ship. From this sanctuary, supporting data bases and staffs provide additional support such as logistics, medicine, and wargaming. US forces dig in and physically protect their components and establish strict emission control. Even in the setup process, forces posture information capabilities to support the division's forward movement.
The division moves forward via multiple routes during this period of extreme vulnerability. Redundant C2 headquarters are pushed forward. The A and B forward CPs have identical capabilities for communications and intelligence. Intelligence and RISTA capabilities are pushed forward early, both for security and to provide overwatch of routes. Key signal nodes are positioned forward to kick in when the unit begins to maneuver, but the division is silent. Strict control on emissions is observed. The Joint Surveillance Target Attack Radar System (J-STARS) provides situational awareness and force tracking. UAVs and satellites extend communications and networks. Units receive updates on the move via satellite broadcasts. Concurrently, the unit begins to shape the battlespace.
When thinking about shaping the battlespace, one must understand the enemy's organizational whole. The targets, tempo, echelon, networks, and groupings are not physical things on the ground; they are entirely C2 concepts. For example, if our intent is to talk about stripping the enemy's artillery, then it is his grouping capacity--his capability to generate his fire plan and maneuver with fires--that we want to attack.
Without a pause in the tempo of the attack, units shift to close combat with maneuver forces. Shaping activities are already isolating the current battle zone and closing off the enemy's capacity for reconnaissance. Decisive combat is possible without defeating the enemy force in detail. This is accomplished by focusing combat power at precise locations that destroy the organizational integrity of the force. Force tracking and predicative tools allow maneuvering where the enemy is not and orchestrate effects not where he is, but where he is going to be.
The intelligence processes reach the crossover point, and organic collections kick in. The commander looks at how the enemy will react to his plan. Complete situational awareness is critical. The communications network and/or tactical internet must be maneuvered to maintain information flow and needed communications capacities to weigh the bandwidth to the main effort. During decisive operations, the information flow reaches a crescendo and so does the potential for information overload. This is where a well-thought-out CCIR comes into play--a schedule that lays out the frequency and character of certain reports. CCIRs need to focus on visualizing the sequence of events that moves the commander from his current situation to an end state.
INFOSYS are consolidated and reconstituted to police up the digits on the battlefield. This is accomplished by repairs on the internet, cleanup, and purging of data bases. Addressees and protocols match actual reorganization, reflecting losses. Forces communicate through the INFOSYS for telemaintenance and telemedicine and call forward combat service support. Repositioning of the INFOSYS for branches and sequels begins.
In almost every case, Army commanders employing C2W can expect to do so in a joint context. But regardless of whether the operation is joint or purely Army, the commander drives C2W in his organization. The operations staff (G3/J3) plans for and executes the C2W plan. The command and staff process for C2W operations is no different than any other, except in the parameter of focus. Joint and multinational C2W planning and the process that follows apply to all levels of war and all echelons.
C2W is inherently joint and multinational. The development of C2W capabilities, plans, programs, tactics, employment concepts, intelligence, and communications support, as a part of military strategy, requires coordination with responsible DOD components and allied and coalition nations. In coalition operations the key to C2W is the need to plan in a multinational manner and achieve a workable multilevel security program. An exchange of LNOs may be the most effective way to secure these objectives.
The joint force conducts C2W efforts around a joint force C2W organization. This may be a C2W cell in a JTF or a C2W battle staff for a CINC. The key to joint employment of C2W is to leverage the needed capabilities from the service or component that has them available and employ them to support the JTF/CINC mission. Just as there is a synergy by employing the five elements of C2W in a synchronized manner, there is a synergy in blending the capabilities of the services to focus on mission accomplishment. CJCSI 3210.03 and Joint Pub 3-13.1 provide joint policy and doctrine on C2W. The ability of service staffs to integrate effectively to support joint operations is critical. Two existing staff elements that may be used to facilitate joint IO activities are the BCE found within corps headquarters and the air/naval gunfire liaison company (ANGLICO) found within most fleet Marine forces. Both already serve as information nodes to coordinate activities across service lines.
Effective C2W planning requires a framework that focuses the battle staff, thereby ensuring a plan that supports the commander's concept of operation by integrating the elements of C2W into a coherent, synchronized plan.
C2-ATTACK PLANNING STEPS
This seven-step process provides a structure and facilitates the planning process for C2-attack.
C2-PROTECT PLANNING STEPS
This seven-step process provides a structure and facilitates the planning process for C2-protect.
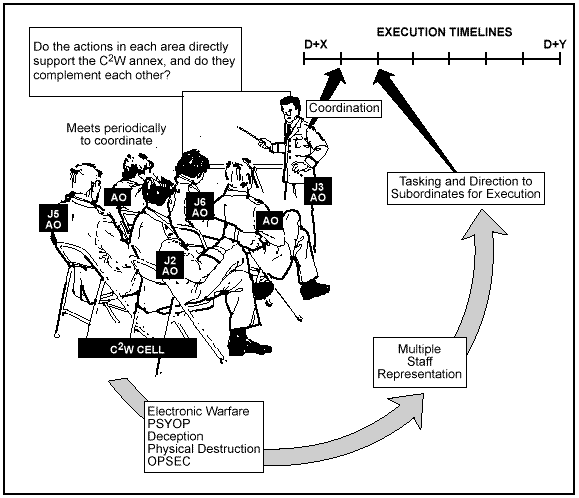
C2W-related information is in the operations, intelligence, and communications-electronics (C3) annexes. For most operations, a C2W annex consolidates and integrates deception, EW, PSYOP, and OPSEC activities into a coherent and cohesive operation. On occasion, based upon METT-T, the commander may elect to produce EW, PSYOP, military deception, and OPSEC annexes as stand-alone parts of the plan or order. The C2W annex includes--
A sample format of the C2W annex to the OPLAN/OPORD is found in Appendix A, Annex B. Coordination of the C2W plan, action, direction, and objectives is illustrated in Figure C-1.
